CJR Wholesale Infrastructure & Security Case Study
CJR Wholesale Infrastructure & Security Case Study
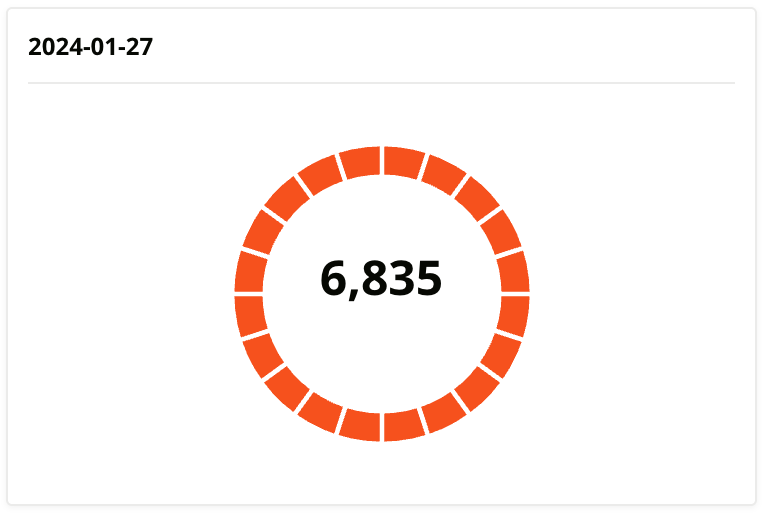
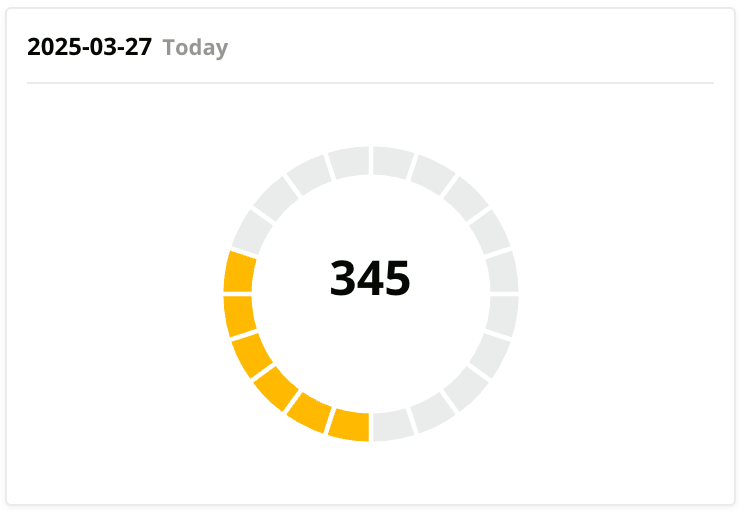
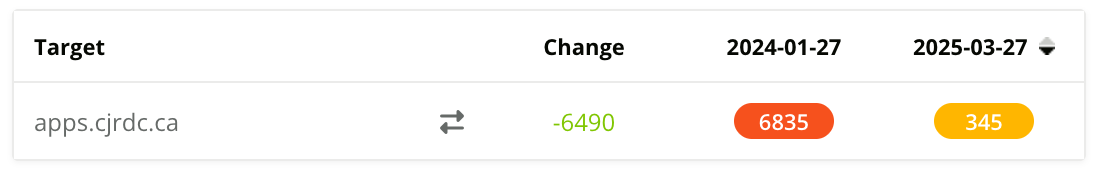
In January 2024, CJR Wholesale had a Halo Security Risk Score of 6835, indicating multiple vulnerabilities across their hosting environment. Most of their infrastructure ran on a shared platform using Rebel hosting (MySQL 5.5.x, PHP 7.2.x, and Plesk) with numerous outdated services, firewall misconfigurations, and SSL/TLS issues. In direct collaboration with Idextrus, they fully migrated to AWS, upgraded software and security protocols, and containerized major applications. After these improvements, CJR Wholesale’s Halo Security score dropped to 345.
* It should be noted, that scores for security audits, as in golf, the lower the number the better.
Challenges and Initial Score
- Firewall Service misconfigurations
- Unpatched SSH vulnerabilities
- Obsolete PHP and MySQL versions
- Outdated certificates leading to SSL/TLS vulnerabilities
- Scalability and performance constraints on shared hosting
- No CI/CD Pipelines
- Limited Bot Mitigation
- Limited Under-Attack Options
- Low Security Awareness
Approach & Migration Strategy
Idextrus applied a “shift-left” security methodology, integrating security at every phase of the migration. The main pillars of our approach included:
- Containerization & Modernization: The legacy MySQL 5.5 and PHP 7.2 stack was upgraded to MySQL 8.x (Aurora) and PHP 7.4.x, wrapping the applications (OMS and EDS) in Docker for portability and rapid deployment.
- AWS Cloud Deployment: Infrastructure was shifted to AWS, employing EC2, EFS, and Aurora RDS for robust scalability. Networking used VPC isolation and improved firewall rules (Security Groups, NACLs) to tackle infiltration risks.
- Asset Decoupling: All static assets were moved outside of the container to S3 and Cloudinary for optimized loading and simplified maintenance.
- Security Hardening & Patch Management: Addressed outdated SSL/TLS certificates, enforced TLS 1.2+ across services, and automated SSH key rotation to patch vulnerabilities.
- CI/CD & Testing: Implemented continuous integration and deployment pipelines to ensure every code push was tested, scanned, and deployed automatically once approved.
- CloudFlare Proxy: The application was proxied to enhance security, performance, and reliability. Additionally, Cloudflare provided DDoS protection, SSL/TLS termination and additional security controls.
Results & Impact
Post-migration, CJR Wholesale re-ran the Halo Security Audit. The score dropped from 6835 to 345 (a 95% risk reduction). Not only were key vulnerabilities addressed, but overall performance improved, and application scalability is no longer a bottleneck.
- Firewall: Fully hardened, with fine-grained Security Groups and NACLs preventing unauthorized traffic.
- SSH: Automated patching and rotation significantly reduced attack surface.
- Software Upgrades: Eliminated technical debt from obsolete versions, ensuring optimal performance.
- Certificates & TLS: Seamless secure connections using AWS Certificate Manager; only TLS 1.2+ protocols allowed.
- DDoS/Bot Mitigation Tools: Web Analytics, tools to manage request routing based on filters (Geo, Device, User, IP), active DDoS protection as well as bot mitigation tools.
- CI/CD: Quicker feature deployment with robust test coverage; less downtime and faster delivery cycles.
Conclusion
Through cloud-native best practices and rigorous security methodologies, Idextrus enabled CJR Wholesale to modernize their infrastructure and reduce risk significantly. The process not only addressed immediate security threats but also laid the foundation for continuous improvement, scalability, and long-term innovation.
Next Steps
Want to learn more? Book a call with Idextrus to discover how we can guide your organization to a more secure and scalable future.

